- Local time
- 7:00 PM
- Posts
- 5,678
- OS
- Windows 10 Pro + others in VHDs
Many of you will be familiar with Pro(+) Bitlocker where you can protect partitions.
In applying Bitlocker to a partition, you are asked to enter a password, and save the recovery key somewhere (MS account or another drive, including USB drive).
If you have a TPM, you do not need to enter password to access drive.
Bitlocker Device Encryption is different and is only available on Windows 10/11 Home if you have
1) TPM and Secure Boot Enabled
2) Modern Standyby
3) You are using MS account.
So if you clean install Windows 10 Home and you can use Bitlocker Device Encryption (note used to be just called Device Encryption), then if you turn it on, it encrypts C drive, and any other data partitions on PC.
There is no password (that is in TPM), but it does store the long recovery code on MS account (one for each drive in fact).
So I thought - how does it work if you install Home as a dual boot option with an existing OS on PC.
So I installed it in a virtual hard drive and created a native boot entry.
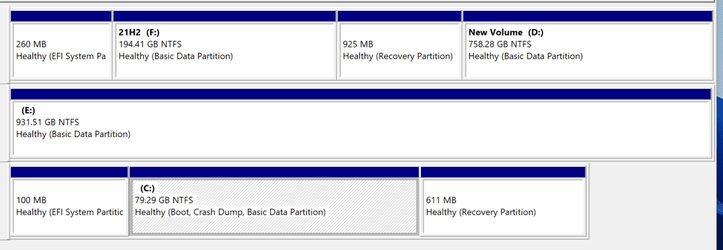
So here is what my laptop looks like.
Drive F is my normal OS (all bascked up with Macrium Reflect in case things screw up in my tests).
Disk 2 is my vhd containing Windows (the EFI and recovery partitions are not relevant as EFI on disk 0 contains boot entry for vhd.
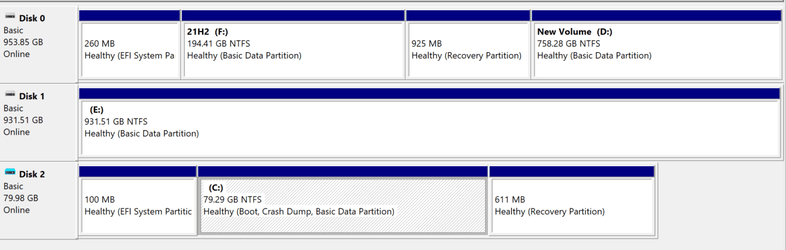
So I turned on bitlocker device encryption,
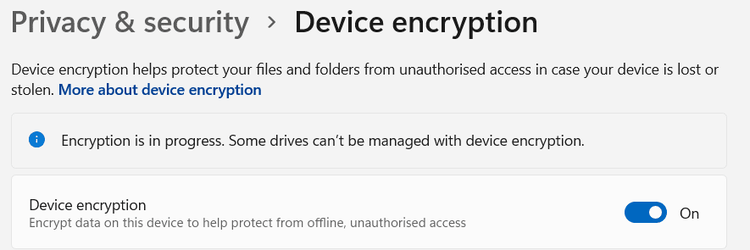
It gave me a warning some drives could not be encrypted.
Quite reasonably, it did not encrypt the F drive (my main OS), as that would be an issue.
It did not encrypt the E drive - I suspect as that is the drive that contains the VHD.
It decided to encrypt the D drive, and if there were other data partitions, it would encrypt those as well I suspect.
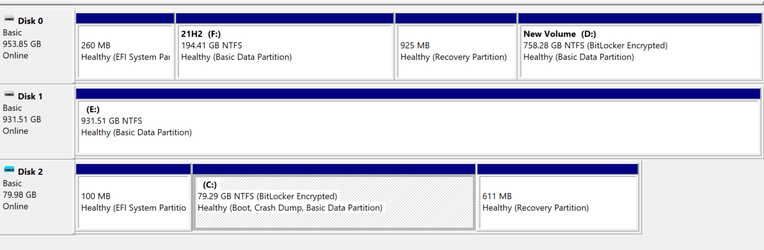
I booted pc back to main OS, and sure enough, I could not access D without using the long recovery code.
There does not seem to be anyway of unlocking D drive but leaving C drive locked.
None of this is a surprise, but it does show you have to be careful using bitlocker device encryption in dual boot pcs, as you could bitlock partitions you do not want to bitlock.
The cack handed way round this was to boot into Pro, then bitlock drive D first (and create password), so it did not get bitlocked by device encryption when encrypting Home. I could access the D drive by entering password.
On thing that would probably be dumb would be to bitlock my drive E in pro, and then try and native boot to vhd on that drive - so here goes in the interest of science......
Well I was pleasantly surprised - if you bitlock a drive containing native boot vhds (with entries on main bcd), it asks you for the password before booting into vhd.
In applying Bitlocker to a partition, you are asked to enter a password, and save the recovery key somewhere (MS account or another drive, including USB drive).
If you have a TPM, you do not need to enter password to access drive.
Bitlocker Device Encryption is different and is only available on Windows 10/11 Home if you have
1) TPM and Secure Boot Enabled
2) Modern Standyby
3) You are using MS account.
So if you clean install Windows 10 Home and you can use Bitlocker Device Encryption (note used to be just called Device Encryption), then if you turn it on, it encrypts C drive, and any other data partitions on PC.
There is no password (that is in TPM), but it does store the long recovery code on MS account (one for each drive in fact).
So I thought - how does it work if you install Home as a dual boot option with an existing OS on PC.
So I installed it in a virtual hard drive and created a native boot entry.
So here is what my laptop looks like.
Drive F is my normal OS (all bascked up with Macrium Reflect in case things screw up in my tests).
Disk 2 is my vhd containing Windows (the EFI and recovery partitions are not relevant as EFI on disk 0 contains boot entry for vhd.

So I turned on bitlocker device encryption,

It gave me a warning some drives could not be encrypted.
Quite reasonably, it did not encrypt the F drive (my main OS), as that would be an issue.
It did not encrypt the E drive - I suspect as that is the drive that contains the VHD.
It decided to encrypt the D drive, and if there were other data partitions, it would encrypt those as well I suspect.

I booted pc back to main OS, and sure enough, I could not access D without using the long recovery code.
There does not seem to be anyway of unlocking D drive but leaving C drive locked.
None of this is a surprise, but it does show you have to be careful using bitlocker device encryption in dual boot pcs, as you could bitlock partitions you do not want to bitlock.
The cack handed way round this was to boot into Pro, then bitlock drive D first (and create password), so it did not get bitlocked by device encryption when encrypting Home. I could access the D drive by entering password.
On thing that would probably be dumb would be to bitlock my drive E in pro, and then try and native boot to vhd on that drive - so here goes in the interest of science......
Well I was pleasantly surprised - if you bitlock a drive containing native boot vhds (with entries on main bcd), it asks you for the password before booting into vhd.
Attachments
Last edited:
My Computer
System One
-
- OS
- Windows 10 Pro + others in VHDs
- Computer type
- Laptop
- Manufacturer/Model
- ASUS Vivobook 14
- CPU
- I7
- Motherboard
- Yep, Laptop has one.
- Memory
- 16 GB
- Graphics Card(s)
- Integrated Intel Iris XE
- Sound Card
- Realtek built in
- Monitor(s) Displays
- N/A
- Screen Resolution
- 1920x1080
- Hard Drives
- 1 TB Optane NVME SSD, 1 TB NVME SSD
- PSU
- Yep, got one
- Case
- Yep, got one
- Cooling
- Stella Artois
- Keyboard
- Built in
- Mouse
- Bluetooth , wired
- Internet Speed
- 72 Mb/s :-(
- Browser
- Edge mostly
- Antivirus
- Defender
- Other Info
- TPM 2.0