- Local time
- 11:27 PM
- Posts
- 129
- OS
- Windows 11 Pro build 26200.5570 (Dev)
Hi.
Current Microsoft Secure Boot Keys will expire in 2026. Therefore, it may be advisable to update the keys manually in advance.
I did the update and it was successful.
If you have bitlocker enabled, you are advised to save your bitlocker keys. You will need them after the secure boot key update. I don't have bitlocker enabled.
In powershell console opened as administrator, you must run the following commands, one at a time:
Set-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Control\SecureBoot” -Name “AvailableUpdates” -Value 0x40
Start-ScheduledTask -TaskName “\Microsoft\Windows\PI\Secure-Boot-Update”
After you run the commands, you have to restart your PC twice for the update to take effect.
To check if the update is successful, you must run the following command in a powershell console with admin privileges:
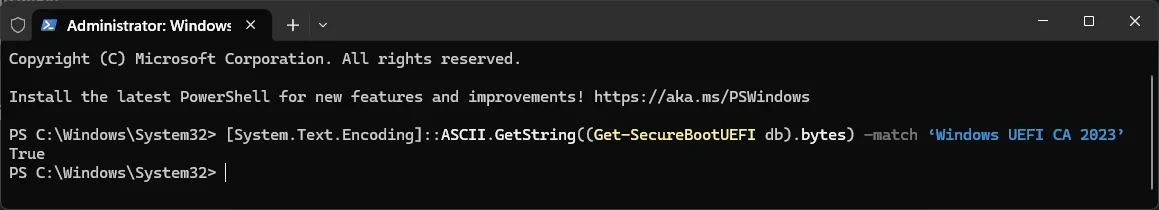
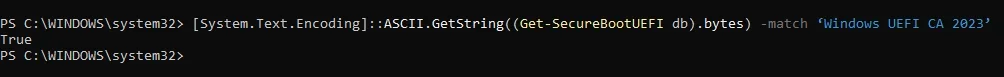
[System.Text.Encoding]::ASCII.GetString((Get-SecureBootUEFI db).bytes) -match ‘Windows UEFI CA 2023’
This command should return the value TRUE. The below screenshot is from my PC. It returned a True value.

For further information, you may refer to the following Microsoft Windows IT Pro Blog:
Updating Microsoft Secure Boot keys | Windows IT Pro blog
Hope you find this post helpful.
Current Microsoft Secure Boot Keys will expire in 2026. Therefore, it may be advisable to update the keys manually in advance.
I did the update and it was successful.
If you have bitlocker enabled, you are advised to save your bitlocker keys. You will need them after the secure boot key update. I don't have bitlocker enabled.
In powershell console opened as administrator, you must run the following commands, one at a time:
Set-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Control\SecureBoot” -Name “AvailableUpdates” -Value 0x40
Start-ScheduledTask -TaskName “\Microsoft\Windows\PI\Secure-Boot-Update”
After you run the commands, you have to restart your PC twice for the update to take effect.
To check if the update is successful, you must run the following command in a powershell console with admin privileges:
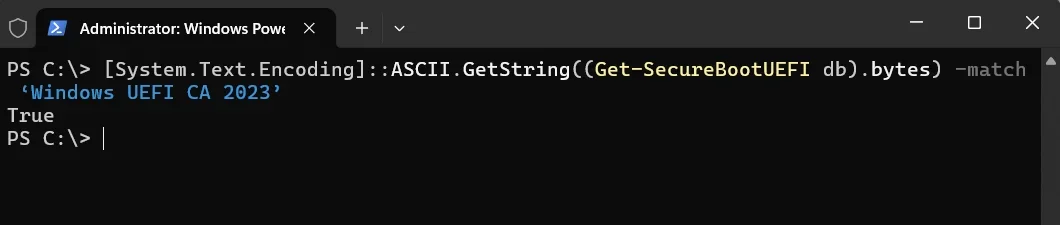
[System.Text.Encoding]::ASCII.GetString((Get-SecureBootUEFI db).bytes) -match ‘Windows UEFI CA 2023’
This command should return the value TRUE. The below screenshot is from my PC. It returned a True value.

For further information, you may refer to the following Microsoft Windows IT Pro Blog:
Updating Microsoft Secure Boot keys | Windows IT Pro blog
Hope you find this post helpful.
My Computers
System One System Two
-
- OS
- Windows 11 Pro build 26200.5570 (Dev)
- Computer type
- PC/Desktop
- Manufacturer/Model
- Home Built
- CPU
- Intel i7-4790
- Motherboard
- Asus H97 Pro Gamer with add-on TPM1.2 module
- Memory
- Teams DDR3-1600
- Graphics Card(s)
- MSI Nvidia GeForce GTX 1050Ti
- Sound Card
- Realtek ALC1150
- Monitor(s) Displays
- LG Flatron E2250
- Screen Resolution
- 1920 by 1080 pixels
- Hard Drives
- Crucial NVMe PCIe M2 500 GB (Windows 11 v.24H2); Samsung SSD Evo 870 500 GB (Windows 11 v.24H2);
- PSU
- Corsair HX850
- Case
- Gigabyte Solo 210
- Cooling
- Zalman CNPS7X Tower
- Keyboard
- Microsoft AIO Wireless (includes touchpad)
- Mouse
- HP S1000 Plus Wireless
- Internet Speed
- 200 Mb fiber optic
- Browser
- Chrome; MS Edge
- Antivirus
- Windows Defender
-
- Operating System
- MacOS 12 Monterey
- Computer type
- Laptop
- Manufacturer/Model
- Apple Macbook Air
- CPU
- Intel Core i5
- Memory
- 8 GB
- Graphics card(s)
- Intel integrated
- Screen Resolution
- 1440 by 900 pixels
- Hard Drives
- 128 GB
- Mouse
- Microsoft Wireless
- Keyboard
- Built-in
- Internet Speed
- 802.11 ac
- Browser
- Chrome; Safari
- Antivirus
- N/A