You surely recall the buggy ASR rule that deleted user's shortcuts?

 techcommunity.microsoft.com
techcommunity.microsoft.com
The link above outlines this bug and also says this bug will trigger for intelligence builds between 1.381.2134.0 and 1.381.2163.0.
I need to programmatically determine if current computer is using the specified "intelligence builds" in PowerShell and if so then I skip enabling this ASR rule.
My problem is that it's unclear what is "intelligence build"?
To get current Windows Defender versions I can run:

Example output:
Which of those 4 numbers listed in the output above correspond to "intelligence build" that was affecting the ASR rule?
Perhaps it is some other property which I didn't include in the sample output.
Same data can be obtained in Windows Defender app in:
Open Windows Defender app -> click "settings" on the bottom left -> click "About" link

Recovering from Attack Surface Reduction rule shortcut deletions | Microsoft Community Hub
Guidance on how to recover from short-cut deletions including PowerShell script.
The link above outlines this bug and also says this bug will trigger for intelligence builds between 1.381.2134.0 and 1.381.2163.0.
On January 13th, Windows Security and Microsoft Defender for Endpoint customers may have experienced a series of false positive detections for the Attack Surface Reduction (ASR) rule "Block Win32 API calls from Office macro" after updating to security intelligence builds between 1.381.2134.0 and 1.381.2163.0.
I need to programmatically determine if current computer is using the specified "intelligence builds" in PowerShell and if so then I skip enabling this ASR rule.
My problem is that it's unclear what is "intelligence build"?
To get current Windows Defender versions I can run:
Powershell:
Get-MpComputerStatus | select AMProductVersion, AMEngineVersion, AntivirusSignatureVersion, AntispywareSignatureVersion | fl
Get-MpComputerStatus (Defender)
Use this topic to help manage Windows and Windows Server technologies with Windows PowerShell.
learn.microsoft.com
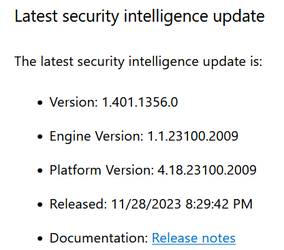
Example output:
Powershell:
AMProductVersion : 4.18.23100.2009
AMEngineVersion : 1.1.23100.2009
AntivirusSignatureVersion : 1.401.1324.0
AntispywareSignatureVersion : 1.401.1324.0Which of those 4 numbers listed in the output above correspond to "intelligence build" that was affecting the ASR rule?
Perhaps it is some other property which I didn't include in the sample output.
Same data can be obtained in Windows Defender app in:
Open Windows Defender app -> click "settings" on the bottom left -> click "About" link
My Computer
System One
-
- OS
- Windows 11 Pro 23H2
- Computer type
- PC/Desktop
- Manufacturer/Model
- MSI / MS-7B29
- CPU
- Intel i3 8100 @3.6Ghz
- Motherboard
- H310M PRO-VDH (MS-7B29)
- Memory
- 1 x 16GB DDR4 @2400 MHz
- Graphics Card(s)
- Nvidia GeForce GT 1030 2GB SDDR4
- Sound Card
- Realtek VEN_10EC&DEV_0887 / NVIDIA VEN_10DE&DEV_0081
- Monitor(s) Displays
- Acer V226HQL
- Screen Resolution
- 1920 x 1080
- Hard Drives
- SSD 500 GB Crucial MX500 / HDD 1 TB TOSHIBA DT01ACA100
- PSU
- ATX, details unknown
- Case
- Everest 551B
- Cooling
- details unknown
- Keyboard
- Mechanical Gaming Hydra R7 - Rampage
- Mouse
- Logitech G703
- Internet Speed
- Down: 28Mbps / Up: 19Mbps
- Browser
- Microsoft Edge
- Antivirus
- Microsoft Defender Antivirus
- Other Info
- Bluetooth: TP Link 5.0 Nano USB adapter UB500
WLAN: D-Link 150 Pico USB adapter, N standard
Web camera: Logitech C270 HD 720p @30fps
Microphone: Trust MICO, model 23790