- Local time
- 9:54 AM
- Posts
- 29
- OS
- W11 Pro
Hi All,
First time using bitlocker and TPM (forced on me by work ).
).
I have 2 Questions for you guys.
Macrium = v8.1.8017
Q1: 'Save to USB Flash' (bkf) option is missing
I am having the same problem as described here:
 www.tenforums.com
www.tenforums.com
when trying to export the bitlocker key for use in Macrium, there is no option to "Save to a USB flash drive"
The only options are save to text file, asure or print.
I also read the information at:
 knowledgebase.macrium.com
knowledgebase.macrium.com
but there seems no way to export the file into a format that Macrium can use.
Is there a way to export this via PowerShell or some way to enable it in Windows 11?
OR is there another format that can be used by Macrium?
I also just spun up a new vm of W11 PRO 23h2 as a test and even in the vm the "save to USB" option is missing so is this no longer an option for Macrium?
If that is the case then why is auto unlock still an option in RMBuilder?
Q2: Mounting a bitlocker image
Even without the "auto unlock" working from Q1, I went ahead and did a backup anyway using the recovery media and all worked as expected, however my question relates to when I try to map the image via the image browser. There does not seem to be a way to look at my data in the image since I have never prompted for the Bitlocker Recovery key. I get an error message Drive XX is not formatted.
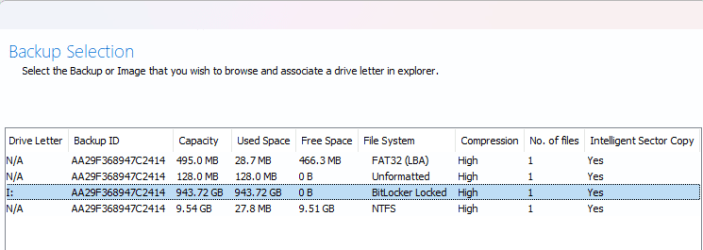
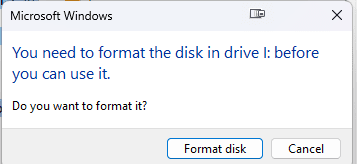
Is this not an option when you are dealing with encrypted drive images and wanting to mount the image on a 2nd computer to browse for a few files to restore - is a full disk restore the only option here to get at the files?
Thanks
First time using bitlocker and TPM (forced on me by work
I have 2 Questions for you guys.
Macrium = v8.1.8017
Q1: 'Save to USB Flash' (bkf) option is missing
I am having the same problem as described here:
BitLocker Save to USB Flash missing? - Windows 10 Help Forums
Hi, I followed the step by step guide on what Brink wrote up below. https://www.tenforums.com/tutorials/3...-a.html?filter[1]=Security System Tools How
when trying to export the bitlocker key for use in Macrium, there is no option to "Save to a USB flash drive"
The only options are save to text file, asure or print.
I also read the information at:
Adding BitLocker support to Windows PE - Knowledgebase 8.0 - Macrium Reflect Knowledgebase
but there seems no way to export the file into a format that Macrium can use.
Is there a way to export this via PowerShell or some way to enable it in Windows 11?
OR is there another format that can be used by Macrium?
I also just spun up a new vm of W11 PRO 23h2 as a test and even in the vm the "save to USB" option is missing so is this no longer an option for Macrium?
If that is the case then why is auto unlock still an option in RMBuilder?
Q2: Mounting a bitlocker image
Even without the "auto unlock" working from Q1, I went ahead and did a backup anyway using the recovery media and all worked as expected, however my question relates to when I try to map the image via the image browser. There does not seem to be a way to look at my data in the image since I have never prompted for the Bitlocker Recovery key. I get an error message Drive XX is not formatted.


Is this not an option when you are dealing with encrypted drive images and wanting to mount the image on a 2nd computer to browse for a few files to restore - is a full disk restore the only option here to get at the files?
Thanks
- Windows Build/Version
- w11 PRO 23h2
My Computer
System One
-
- OS
- W11 Pro