Safeguard holds are one of several previously announced protection features of the Windows Update for Business deployment service. In this article, we explore how you benefit from safeguards to protect devices under your management during deployments. Specifically, we'll review:
Earlier this year, we started a new blog series exploring these features, which are designed to work together to help you have a smoother experience when updating and upgrading your organization's devices. These features are available to organizations with Windows 10/11 Enterprise E3 or greater, including Education variants. The first such feature we explored was Gradual rollouts with the Windows Update for Business deployment service. Gradually rolling out the update to intelligently ordered waves of devices reduces risk and gives IT pros more confidence in deployment success. If you haven't read this article, I recommend you check it out! Millions of devices managed by IT have been upgraded to the latest Windows using gradual rollouts to simplify the process and reduce deployment risks.
- Safeguard holds for known and likely issues
- What safeguard holds look like behind the scenes
- How to make the most of safeguard holds
Safeguard holds for known and likely issues
If you have been using the Windows Update service to deploy a new version of Windows to your devices, you have already benefited from safeguard holds for known issues. This includes all Windows Update for Business users. When you go beyond traditional client policies and enroll in the Windows Update for Business deployment service, this protection is expanded to safeguard holds for likely issues as well. Let's define these types of issues and see how they work.
What's a known issue?
A known issue is a problem that may occur after an upgrade that was discovered by Microsoft or reported by a customer or partner. This issue has been evaluated and confirmed for a specific set of devices.
What's a likely issue?
When some devices face complications after an upgrade to Windows 11, protecting customers' devices quickly is a priority. In addition to safeguard holds for known issues, the deployment service utilizes machine learning (ML) performed across millions of unmanaged, daily consumer and commercial PCs installing the upgrade. It looks for any evidence of rollback during setup, an app or driver malfunction, graphics, audio or connectivity issue, etc. When upgrade problems like these surface, this ML spots correlations among device hardware and software characteristics to identify a larger set of devices that have not yet started the upgrade and automatically safeguards them. While this early correlation is not yet a confirmed (known) issue, it is a likely issue. Essentially, where there is smoke, there is often fire, and safeguarding likely issues offers a quicker and higher protection level for such devices.
What safeguard holds do to protect your devices
If Microsoft finds a potential quality or compatibility issue, the safeguard hold feature automatically pauses updates to just those devices that are identified as exposed or at a high risk of exposure. Figure 1 illustrates how an update is paused before the deployment service offers it to devices under your management.

Safeguard holds in action: Diagnostic data from device upgrades not managed by IT informs the deployment service to pause an update deployment to devices under your management.
What safeguard holds look like behind the scenes
That's all great, but how does it really work? Let's look closer at how issues are identified and the process of safeguarding your devices, including the lifespan of these protective measures.
Identifying known issues
We receive feedback from many different channels that tell us about known issues with a Windows update. Feedback comes from partners, customers, Windows Insiders, and our own internal testing process. Once we identify issues that may impact devices after upgrade, we build device-specific criteria that are delivered to impacted devices as a safeguard hold. Safeguarded devices are then paused from updates until the issue has been mitigated.
Identifying likely issues
To make safeguarding likely issues possible, pattern mining is used across millions of daily devices installing the upgrade from Windows Update that are not managed by IT. Specifically, machine learning is applied to the diagnostic data from our broad device ecosystem to automatically identify patterns correlated with update-related disruptions. Data from customer devices using Windows Update for Business is always used in accordance with the Microsoft privacy policy. Figure 2 shows an abnormal failure pattern peaking at 82% against a baseline rate of about 3%.
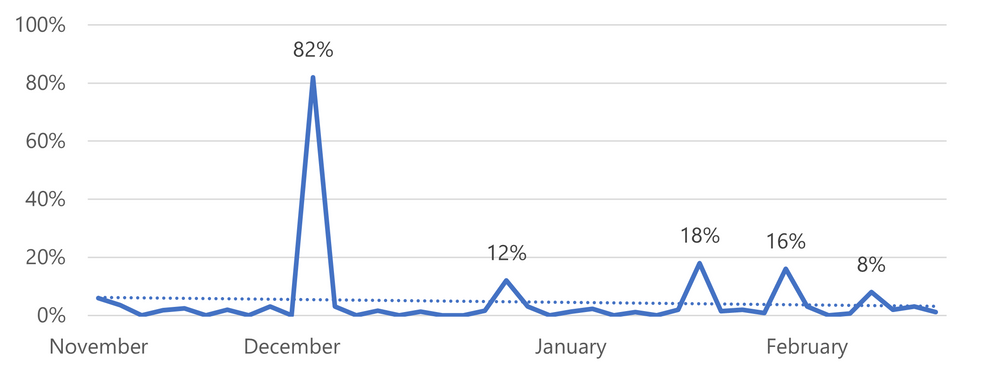
Abnormal update failure pattern across time (adapted from: Using machine learning to improve the Windows 10 update experience)
A pattern refers to a specific combination of attributes. These include hardware characteristics, drivers, and applications – the same attributes that determine device assignment to waves in gradual rollouts. For example, a pattern may reveal an incompatibility between driver X and a third-party app Y on the same device.
The process of safeguarding your devices
Once the machine learning algorithm finds this pattern, it triggers a temporary safeguard hold for a likely issue. Its lifespan varies in duration and prioritizes safety over progress to preserve end user experience and IT peace of mind. The delay allows you a few weeks to make an informed decision on how to proceed with the update to keep your device population protected and productive. We aim to address the temporary hold for a likely issue in four to six weeks by either:
If Microsoft verifies the issue and confirms that the device is indeed not ready to update (scenario a), the safeguard hold transitions to a known issue and continues to delay the device's upgrade until a mitigation is applied. If Microsoft verification deems the likely issue to be a false positive or more scoped in nature (scenario b), the temporary safeguard hold is removed for unaffected devices so the upgrade may proceed, if approved by IT.
- Confirming and transitioning the likely issue to a known issue with safeguard hold maintained.
- Identifying a false positive and automatically removing the hold so devices begin updating.
Microsoft uses two guiding reasons for issuing an automatic safeguard hold for likely issues:
Windows Update maintains a safeguard hold until Microsoft investigates, develops, and validates a fix before offering it to affected devices and restoring the update deployment. Once a fix or mitigation is delivered via Windows Update or a third party, the safeguard hold is lifted, and the device can be offered an update. This ensures a seamless protection experience for end users and IT.
- We have also paused deployment to consumer devices likely exposed to the issue.
- The issue is under active investigation by Microsoft engineers.
How to make the most of safeguard holds
Enable safeguard hold protections to maximize your update deployment experience today! These capabilities are available to you through the Microsoft Graph, PowerShell SDK, Intune, and Update Compliance. Deployment scheduling controls are always available. However, to take advantage of the unique deployment protections tailored to devices under your management, configure devices to share diagnostic data with Microsoft and leverage available reporting tools.
Ensure device prerequisites are met
Safeguard holds apply to Windows Update for Business deployments by default. We do not recommend opt-outs or manual updates, except for strict IT environments and for validation purposes only.
- Diagnostic data must be set to Required or Optional.
- The AllowWUfBCloudProcessing policy must be set to 8 (see how to do so in Microsoft Endpoint Manager, using Group Policy, or mobile device management).
Monitor safeguard holds reporting
If you are affected by a safeguard hold, you will get additional insight into the issue through the M365 Admin Center or the Known Issues sections of the Windows release health dashboard online. You can also monitor your device population with up-to-date reporting.
If you use Update Compliance, you can check your safeguard hold report to see which devices under your management are affected by which safeguard holds. The same information is presented in two different views: the total safeguard hold view (see Figure 3) and device view, which you can sort device by device. While all safeguard holds are marked with an 8-digit identifier, the safeguard hold ID value for all likely issues is 00000001.
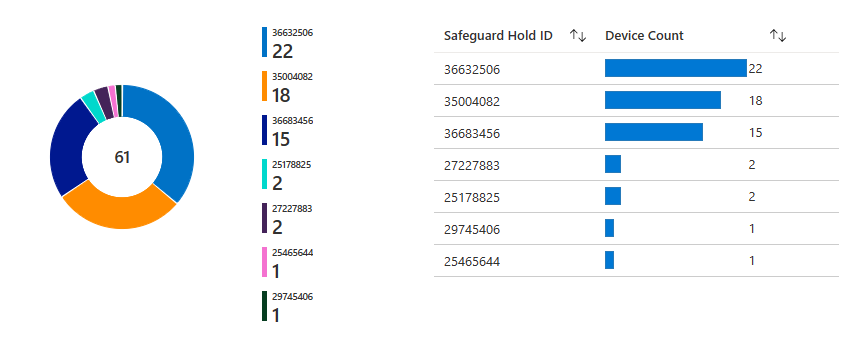
The Update Compliance total safeguard holds view.
(Source: Update Compliance - Safeguard Holds report)
If you use Intune, safeguard holds are now visible in the Feature Update Failures Report. For additional ways to monitor and report on safeguard holds, refer to the documentation of your management solution, such as Am I affected by a safeguard hold?
Stay in the know!
Safeguard holds offer tailored solutions to your environment. This feature is informed by partners, customers, and the latest Microsoft machine learning efforts around known and likely issues that emerge while we are updating the broad ecosystem of devices. That said, we would love for you to join one of our early validation programs to discover any potential issues even before your organization-wide deployment:
This information on the workings of safeguard holds for known and likely issues is meant to prepare you to optimize your update deployment experience. Together with the gradual rollouts feature of Windows Update for Business deployment service, safeguard holds serve to give you additional peace of mind and keep your organization even more protected and productive.
There is more to explore, and our next blog in the series will continue this topic by focusing on automated rollback monitoring. Enjoy the new features available to you through the deployment service and let us know what you think in the comments below or on the Windows Tech Community!
For additional context, visit our existing publications:
- Windows Update for Business deployment service (Docs)
- Access safeguard hold details with Update Compliance (Windows IT Pro Blog)
- Safeguard holds (Docs)
Source:

Safeguard holds with the Windows Update for Business deployment service | Microsoft Community Hub
The Windows Update for Business deployment service can help protect your devices from known or likely issues. Learn how. Explore safeguard holds within the...












