The steps to protect W10 systems are identical to W11, the newer boot files are already available from the current Monthly Updates.
Because W10 22H2 will enter End-of-Life for consumer Windows on Oct. 2025, it's not clear whether MS will force an update before then, or expect users to perform the mitigation as a voluntary procedure.
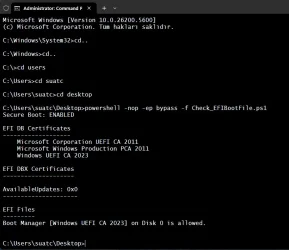
The script posted above will report what certificates are present in the DB (allowed) and DBX (banned) lists.
Ideally, you will have both CA 2011 & CA 2023 as added (both boot files allowed), and DBX may or may not have CA 2011 banned. Not banning CA 2011 doesn't impact Windows, as long as you have both certificates for DB. It just means your system is still vulnerable to an UEFI attack.