JustRebootit
New member
- Local time
- 11:52 PM
- Posts
- 4
- OS
- Windows 11
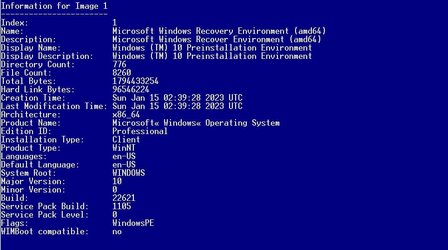
I thought it was something along those lines but wanted to get others input on the subject.2004 and all versions up to 22H2 share a common set of system files. From 2004 up to 22H2 all new features have been delivered in the cumulative updates, but in a dormant state. Each Feature Update was done by means of installing an Enablement Package that turned on the new features and bumps up the major build number by 1, the 22H2 update taking it to 19045.
The ISO for 19045 contains the 19041 system files, plus the 22H2 Enablement Package which it will install at the same time.
View attachment 50004
Thanks
My Computer
System One
-
- OS
- Windows 11