Heya folks, Ned here again. Beginning in Windows 11 Insider Preview Build 25951 (Canary), the SMB server now supports controlling which SMB 2 and 3 dialects it will negotiate. This changes legacy behavior, where Windows SMB server always negotiated the highest matched server dialect from SMB 2.0.2 to 3.1.1 clients. Beginning in Windows 10, support was added for controlling SMB client dialects, but not server dialects.
With this new option, an administrator can remove specific SMB protocols from usage in the organization, blocking older, less secure, and less capable Windows devices and third parties from connecting. For example, they can specify only the use of SMB 3.1.1, the most secure dialect of the protocol.
Configuring SMB dialect min and max
You can configure this option with Group Policy and PowerShell. Both SMB client and server now include complete management support (previously the client support was only manual registry editing).
Group Policy (SMB Server)
To configure SMB dialect minimum and maximum for the SMB server (i.e. for inbound connection), enable the group policy under:
Computer Configuration \ Administrative Templates \ Network \ Lanman Server \ Mandate the minimum version of SMB
Computer Configuration \ Administrative Templates \ Network \ Lanman Server \ Mandate the Maximum version of SMB
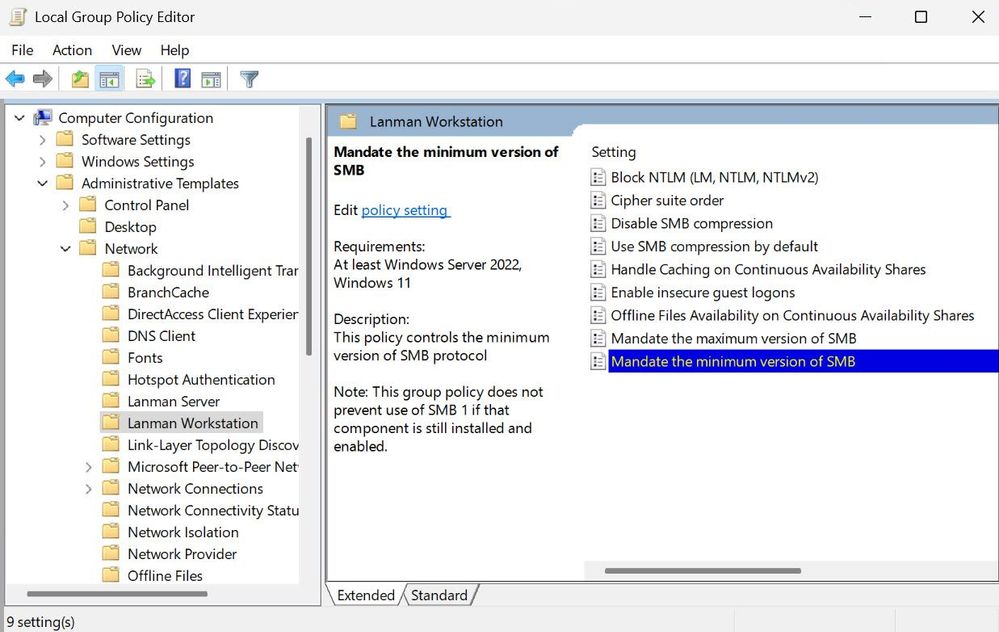
gpedit view of the policy
Select the minimum and maximum version of the dialects using a dropdown menu when the policy is enabled.
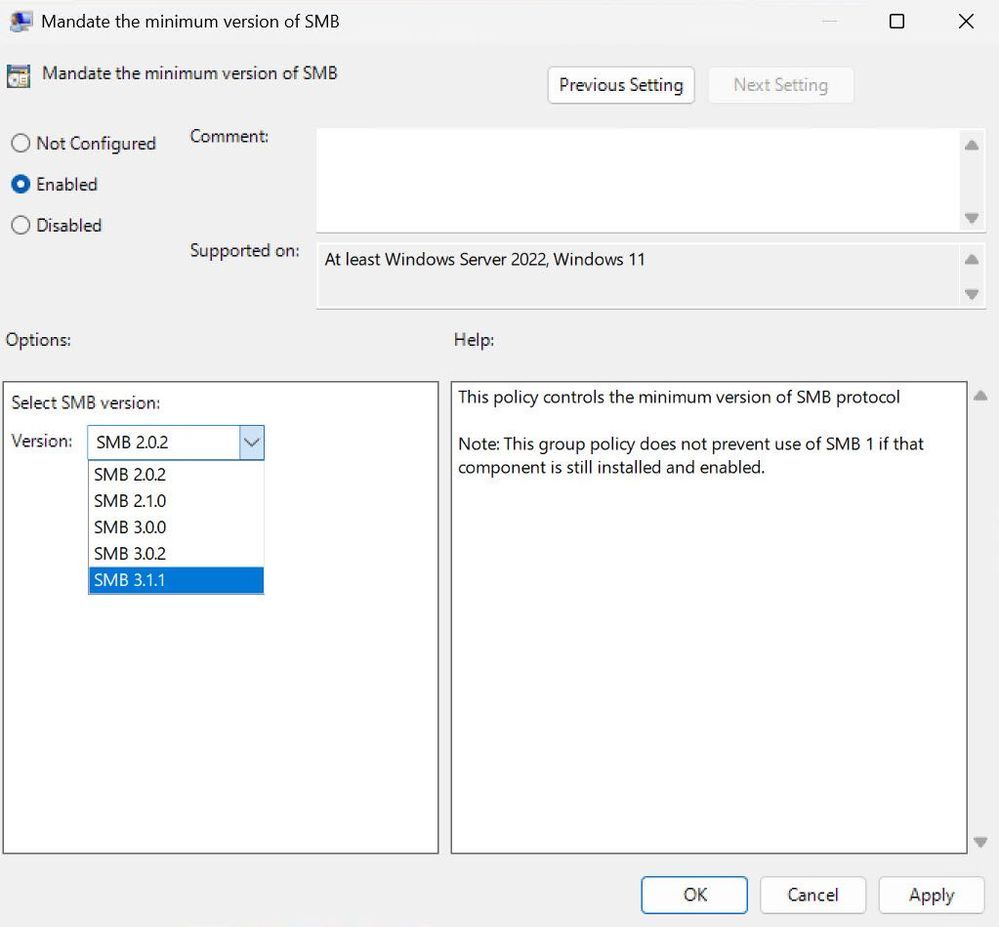
gpedit view of the policy dropdown
Group Policy (SMB client)
To configure SMB dialect minimum and maximum for the SMB client (i.e. for outbound connection), enable the group policy under:
Computer Configuration \ Administrative Templates \ Network \ Lanman Workstation\ Mandate the minimum version of SMB
Computer Configuration \ Administrative Templates \ Network \ Lanman Workstation \ Mandate the Maximum version of SMB
Select the minimum and maximum version of the dialects using a dropdown menu when the policy is enabled.
PowerShell (SMB server)
To configure SMB dialect minimum and maximum for the SMB server service (i.e. for inbound connections) with PowerShell, set with the following syntax:
Set-SmbServerConfiguration -Smb2DialectMax {SMB202 | SMB210 | SMB300 | SMB302 | SMB311 | None} -Smb2DialectMin {None | SMB202 | SMB210 | SMB300 | SMB302 | SMB311}
PowerShell (SMB client)
To configure SMB dialect minimum and maximum for the SMB client service (i.e. for outbound connections) with PowerShell, set with the following syntax:
Set-SmbClientConfiguration -Smb2DialectMax {SMB202 | SMB210 | SMB300 | SMB302 | SMB311 | None} -Smb2DialectMin {None | SMB202 | SMB210 | SMB300 | SMB302 | SMB311}
Final notes
To see this new behavior in action, use a network capture tool like Wireshark and examine the client and server responses for the SMB2 Negotiate Protocol. For instance, here the client requests only SMB 3.1.1 because it's been configured with a minimum and maximum dialect of 3.1.1:
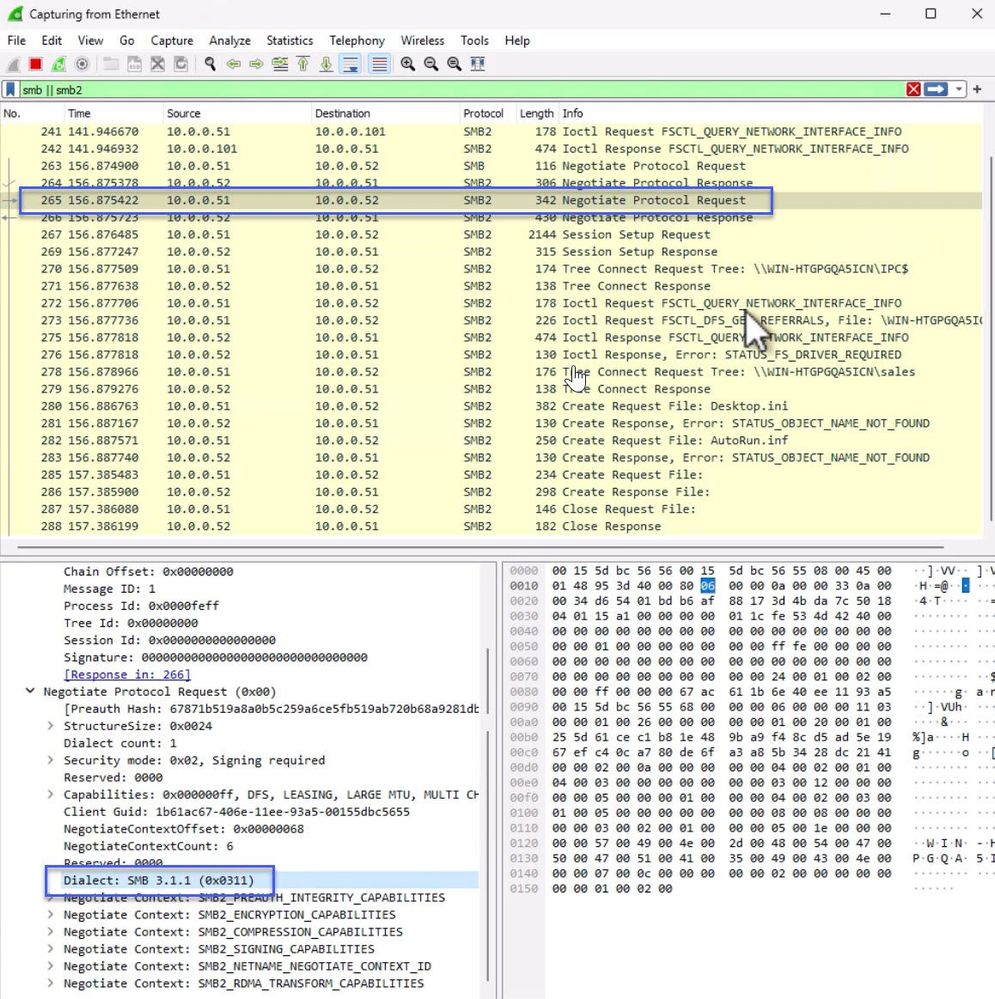
wiresharek capture showing an SMB session creation
This is part of a campaign to improve the security of Windows and Windows Server for the modern landscape. You've read my posts on SMB security changes over the past year:
For more information on securing SMB on Windows in-market, check out:
- SMB NTLM blocking (September 2023)
- SMB signing required by default in Windows Insider (June 2023)
- The beginning of the end of Remote Mailslots (March 2023)
- SMB insecure guest auth now off by default in Windows Insider Pro editions (January 2023)
- SMB authentication rate limiter now on by default in Windows Insider (September 2022)
- SMB1 now disabled by default for Windows 11 Home Insiders builds (April 2022)
Until next time,
- SMB security enhancements | Microsoft Learn
- Secure SMB Traffic in Windows Server | Microsoft Learn
- Protect SMB traffic from interception | Microsoft Learn
Ned Pyle
Source:
SMB dialect management now supported in Windows Insider
SMB now supports controlling SMB2 and 3 dialect usage discretely.
techcommunity.microsoft.com























